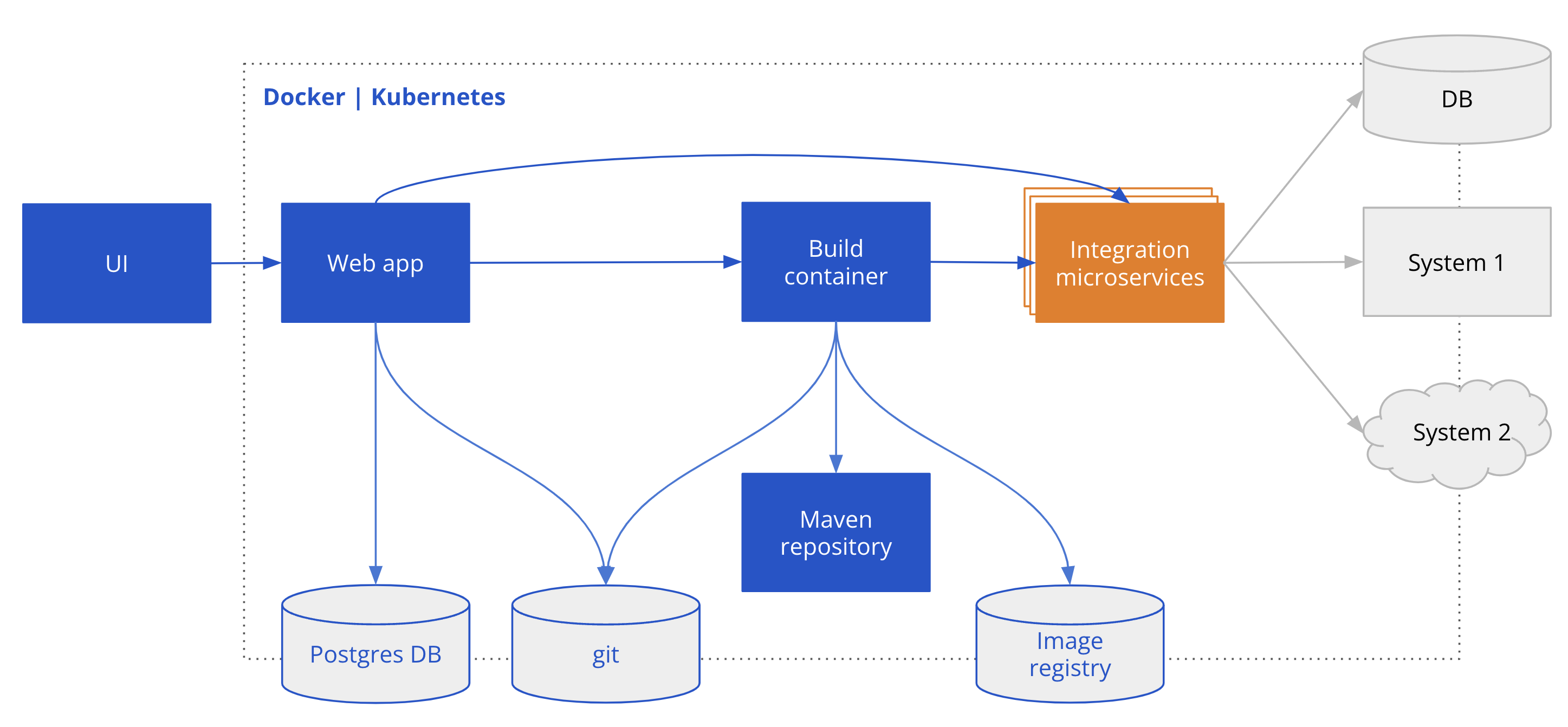
Architecture
Overview
The Talisman Platform is designed with modern deployment practices in mind, offering unparalleled flexibility for integration within various container orchestration environments. It can be seamlessly deployed as a container into Docker, Kubernetes, or OpenShift, catering to the diverse infrastructure needs of organizations. This flexibility ensures that Talisman can be integrated into existing workflows with minimal disruption, leveraging the scalability, resilience, and management capabilities of containerized environments.
Talisman Platform Components
- Web app: Acts as the central interface for the platform, allowing users to manage and orchestrate their integration projects.
- Build Container: Started by the Web app to run integrations in developer mode (dev-mode), package and deploy integrations.
- Maven Repository: Out-of-the-box Maven Repository mirror to keep necessary dependencies required for the project builds.
Auxiliary Components
-
Git: Git repository stores all essential project files, including integration YAML configurations, application.properties, container configurations, deployment resources, and templates. It is considered the source of truth for the application.
-
Image Registry: An Image Registry is used by the Talisman Platform to store container images that are generated during the build process.
-
Postgres DB: Postgres Database is required to store Talisman Platform runtime technical data like integration statuses, healthcheck, and metrics. Talisman Platform does not store any integration routes data in the database.
Optional Component
-
Open Telemetry Service: The platform might be integrated with Open Telemetry to provide observability features such as tracing, metrics, and logs.
-
Keycloak: In case of using OIDC instead of build-in authentication, we recommend to use Keycloak, an open-source OIDC, identity and access management solution that offers features like single sign-on, user federation, and access control to secure applications and services.